Concepts
This chapter will introduce the concepts and terminology of the Kertos platform. It was built to resemble many legal procedures with automation and integration of customer's systems in mind. Therefore, you will find several terms from the GDPR which have been integrated in the Kertos application. They are combined with Kertos specific terms, which are mostly related to the technical nature of the process.
Please be aware that Kertos might implement certain legal terms (in particular those from GDPR) in a modified way, which might deviate from the original legal definition! However, this is a technical interpretation of the legislation and aims to stay close to original definitions.
Kertos Architecture
Kertos translates end user requests to system related actions and helps to manage those procedures. Throughout the process different Kertos users are involved which facilitates execution. But before the actors are introduced, a few terms have to be clarified:
Data Subject Request
The data subject request is the central, initiating object for the flow in Kertos. Most often this is a direct request from a customer or employee triggering a data privacy related action. For example, a customer could request the deletion of their data or access to their personal information. Kertos differentiates 5 different categories of requests:
Access: Request to access personal data
Rectify: Request to change or adjust any personal data
Restrict: Request to restrict access to certain personal data
Delete: Request to delete personal data
Other: Further Requests
Upon reception, a Data Subject Request is then logged and usually turned into the respective System Tasks, which will be explained next. Kertos currently fully automates Access and Deletion requests for the supported systems.
System Task
In order to manage and execute data privacy operations on customer systems, the application makes use of System Tasks. The most common use case is a Data Subject Request (see above) that will lead to the instantiation of multiple, related System Tasks. Take, for example, the deletion request of a customer. This request now results in related System Tasks for every system that deals with customer data. In this sense, it constitutes the technical representation of the customer's request, as there are usually dozens of systems that contain personal data of the customer. As a consequence, a single request mostly relates to multiple System Tasks, forming a 1 to n relationship (1 Data Subject Request = n System Tasks).
System Task refers to a task, that will be executed on a customer's system! It does not refer to how Kertos schedules and queues any application jobs!
Kertos Three Step Process.
To ensure a GDPR compliant process, the Kertos system executes a three-step deletion process: READ - DELETE - READ. In detail, this means, that each deletion process consists of three consecutive steps: First, the data of the Data Subject is searched for and read out in a system (read). This is followed by the actual deletion process (delete). In order to ensure that all data of the Data Subject has been deleted, the data is read out again in the system (read). Only when no more data can be found has the deletion process been successfully completed.
After clarifying the core objects that the application revolves around, the next section will introduce the actors and users of the system.
Data Subjects
Data subjects are the most important external actors in the Kertos ecosystem. In general, a data subject is a person that wants to act on their own personal data, which is being stored at a particular organization. To express their intention, they send a request to the respective company, stating the inquiry related to their data. For example, a customer of an online shop might call the service desk to ask for access to all the data that was collected. Another request might be extracted from an email of an employee demanding all data related to that person to be deleted. Kertos helps to collect those requests from all communication channels and facilitates their execution within the legal timeframe. This includes required policies and procedures, like the verification of Data Subjects, to prevent unauthorized access.
Data Protection Officer
This actor ensures the integrity of the data privacy policies and procedures and was derived from the GDPR regulatory framework. Within the application, the DPO will be mainly concerned with handling Data Subjects requests. Their responsibilities include communication with Data Subjects, distributing and managing subsequent tasks, and meeting request deadlines. Kertos is designed to automate the procedures and help the DPO in carrying out those tasks. To fulfill that purpose, it separates the DPO and their requests from the IT-oriented System Owners and their System Task into two areas of responsibility.
System Owners
The System Owners have to collaborate with the DPOs to facilitate the technical execution of requests on their systems. As the owner of one or multiple systems, their obligation is to enforce the data protection procedures required by the regulations. They are responsible for the translation of incoming Data Subject Requests into the executable System Tasks. In case Kertos is integrated for a particular system, this execution will be automatically triggered for each request. This makes System Owner intervention only necessary on a few rare occasions.
Process Flow
Here you can see the depiction of the implemented process with all related terms on a reduced, abstract level.
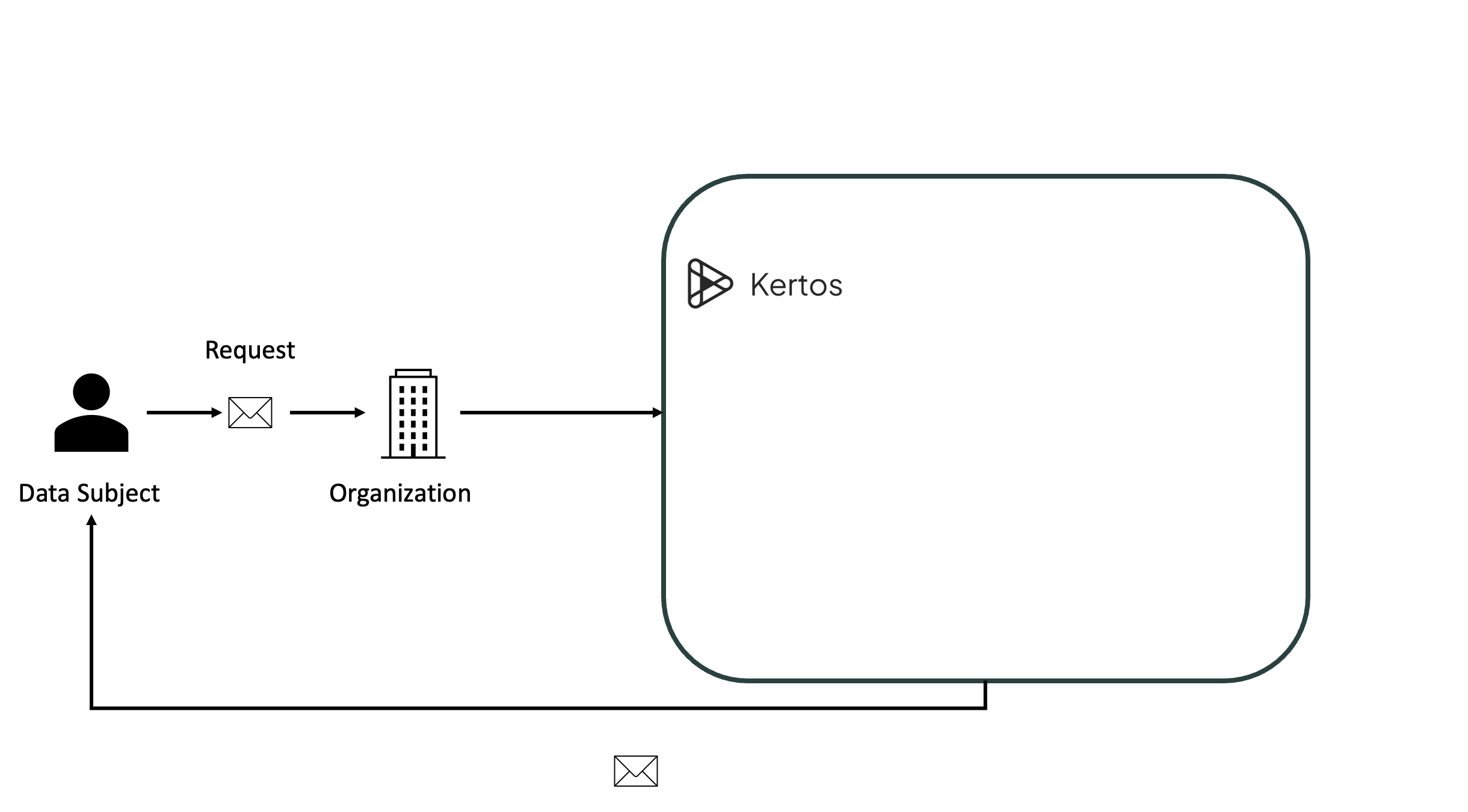
The process initiation starts with the Data Subjects transmitting their requests to the organization. Note that this can be achieved in any form of communication like email, telephone, or physical mail. After reception, the organization transfers the incoming data subject request to the Kertos platform. There are several ways to facilitate this transfer, be it via the automated forwarding of the request from an inbox or service tool or just by manually entering the request.
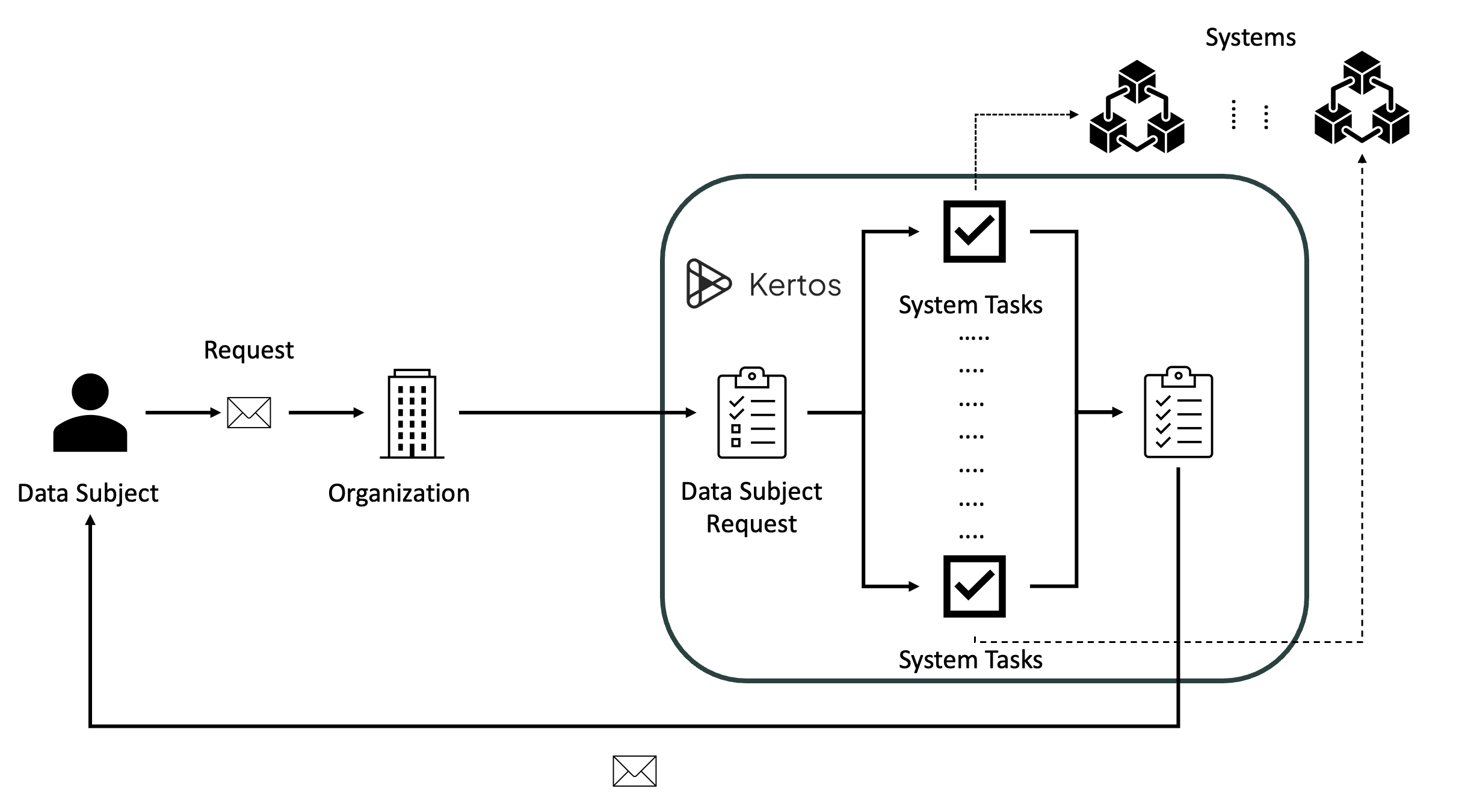
Within the platform, the request generally translates to several related System Tasks, one for each system that contains the data subject's related personal data. This usually covers a broad range of different systems like customer relationship management applications or marketing mail services. After all tasks have been completed, the platform reports the result back to the requesting Data Subjects. In order to meet the legal deadlines of the request, Kertos keeps track of the exact reception dates and informs the relevant stakeholders. All of the flows in Kertos can optionally be accompanied by a human in the loop, making sure that the organization keeps full control.
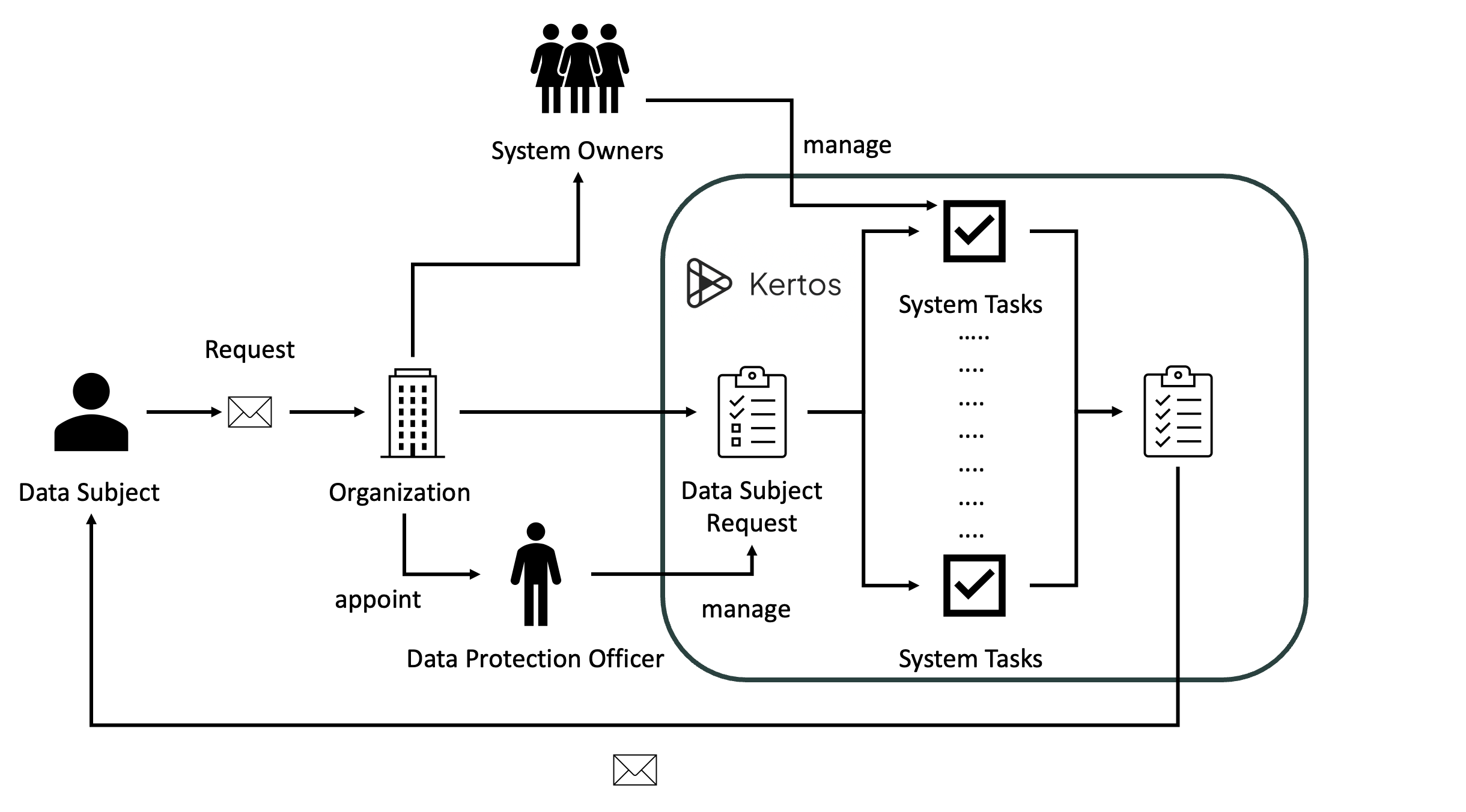
In the platform, the responsibilities are distributed among the Data Protection Officer and the System Owners. While the Data Protection Officers manage the Data Subject Requests, they collaborate with the System Owners, receiving the related System Tasks. Kertos facilitates this collaboration by providing features like reminders, comments and mentions. By integrating the systems and communication channels into the platform, Kertos can automatize this process reducing workload and saving cost. The degree to which the Data Protection Officers and Systems Owners are involved is fully adjustable by the organization.
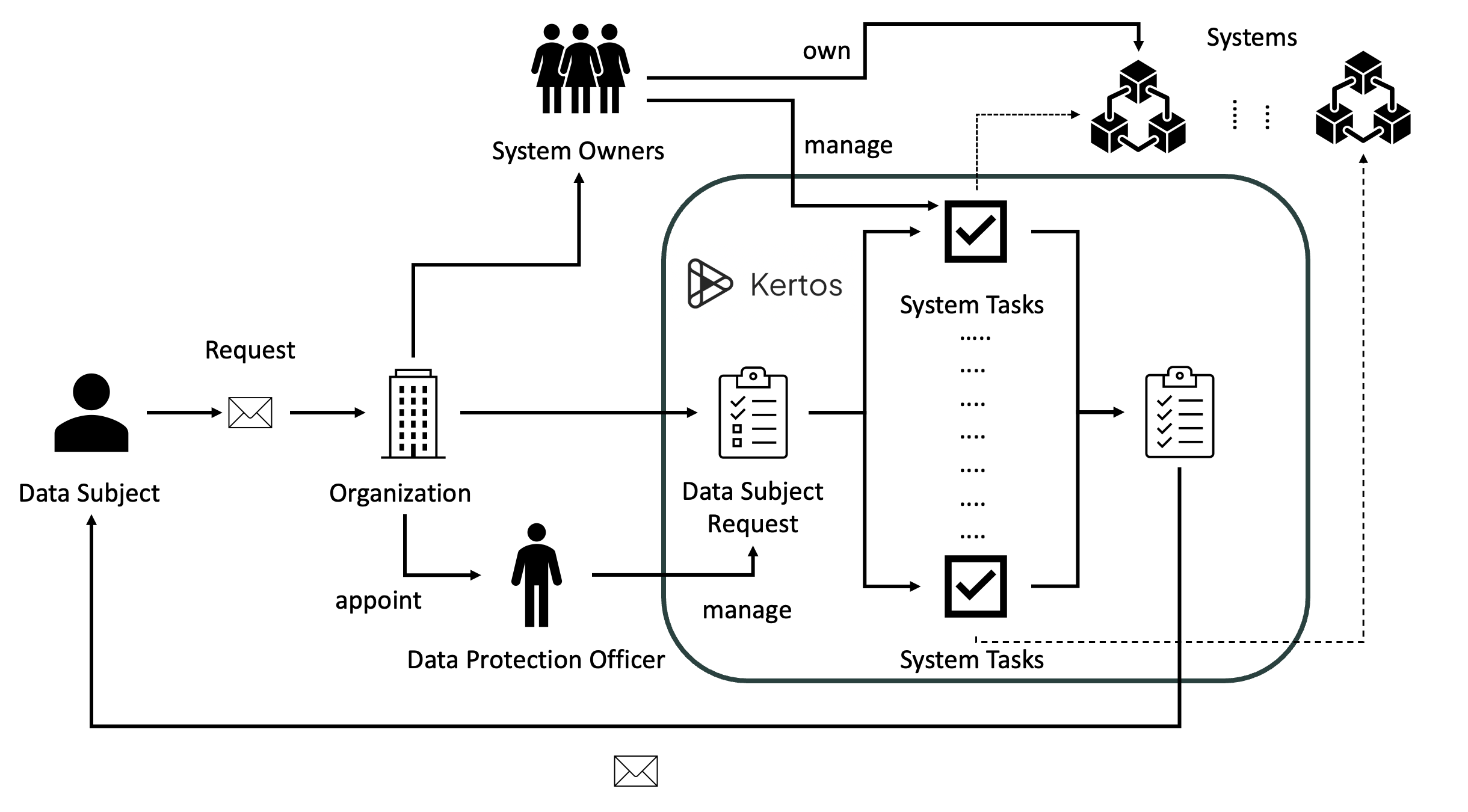
As you can see, Kertos covers the whole end-to-end process to assist organizations with all data privacy related operations. It thus removes tedious process documentation and puts an end to chaotic, error-prone spreadsheet maintenance.