Inventorization of assets
Overview: Classifying and Managing Your Assets for Compliance
In the context of information security, assets are resources that have value to your organization and require protection. These assets are classified as either Primary or Supporting, depending on their role and impact on your business operations.
- Primary Assets are core business processes and critical information that must be protected (e.g., customer data, intellectual property, financial records, HR data).
- Supporting Assets are the infrastructure and tools that enable or process Primary Assets (e.g., databases, software, cloud services, and physical locations).
By linking Primary Assets to their Supporting Assets, Kertos helps you understand how risks impact business processes, ensuring the appropriate security controls are in place.
Key Benefits
- Automated Asset Discovery: Kertos automatically suggests the most relevant Primary Assets based on the systems you’ve integrated, eliminating the need for manual classification.
- Clear Asset Categorization: Easily distinguish between Primary and Supporting Assets, helping you manage and assess your resources effectively.
- Improved Risk Management: Link Primary Assets to Supporting Assets and risks to see how vulnerabilities might impact your business processes and ensure appropriate security measures.
- Comprehensive Compliance: Maintain an up-to-date and complete asset inventory for audit readiness and compliance with frameworks like ISO 27001.
How It Works
1. Discovering and Adding Primary Assets Automatically
Kertos can automatically suggest Primary Assets based on the systems you have listed under the Active Systems tab. This automatic classification ensures all critical assets are captured without the need for manual input.
- Supporting Assets are Activated
When you add a new system (e.g., HubSpot, Salesforce, AWS), it is listed under Active Systems. Kertos detects this automatically. - Primary Assets are Suggested
Kertos suggests the most relevant Primary Assets based on the system detected. For example, if you add HubSpot, Kertos will suggest Lead Scoring and CRM Data as Primary Assets. - Activate Suggested Primary Assets
Suggested Primary Assets appear in the Discovered tab for your review. You can activate these assets with one click, ensuring your asset inventory remains complete.
If a Primary Asset isn’t automatically detected, you can add it manually (see below).
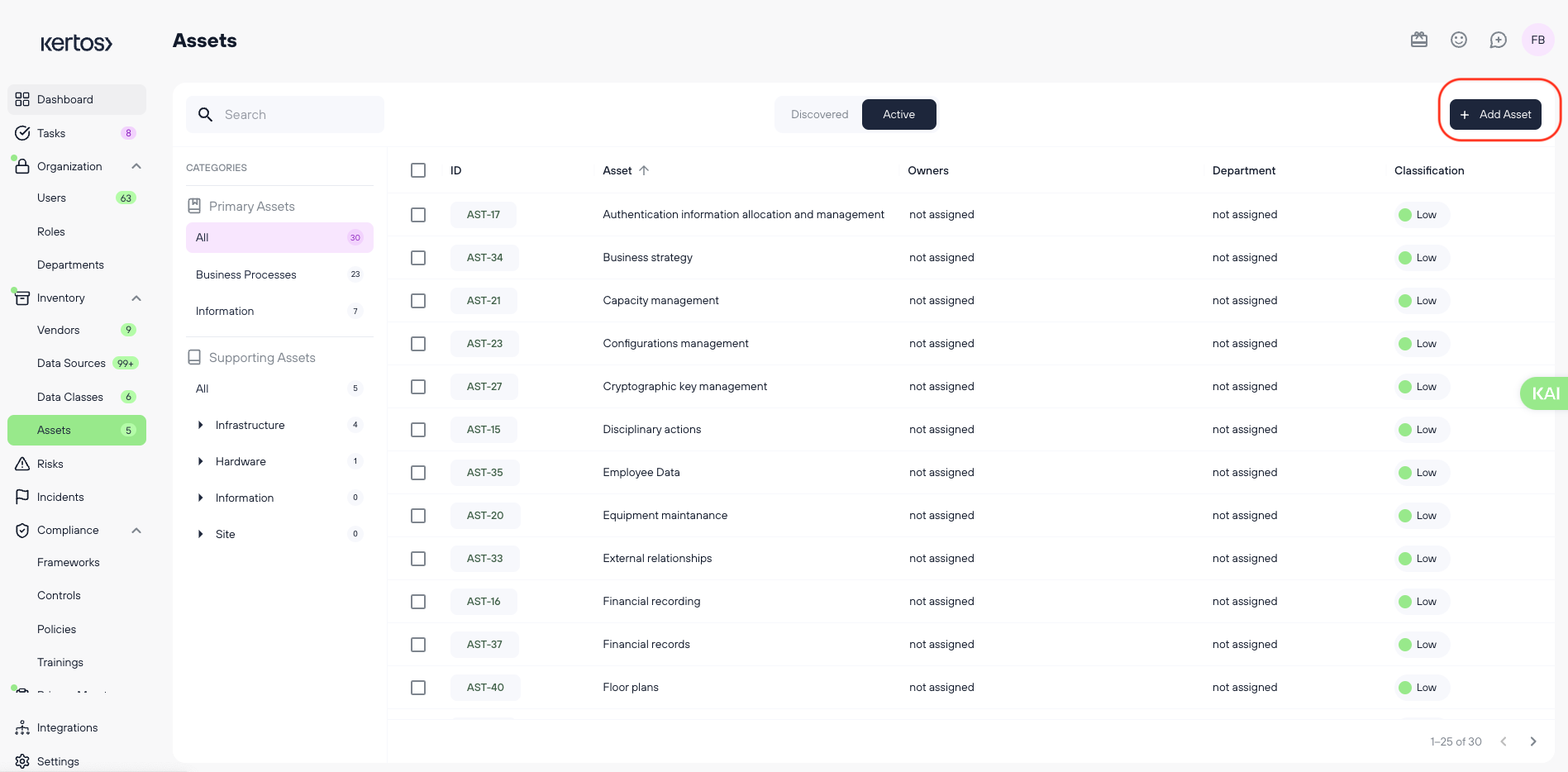
2. Adding Primary Assets manually
If Kertos does not detect a Primary Asset during discovery, you can manually add it.
Steps:
- Navigate to the Assets section in Kertos.
- Fill out the necessary information:
- Asset Name (required)
- Asset ID (required)
- Classification based on the CIA triad (Confidentiality, Integrity, Availability) (required)
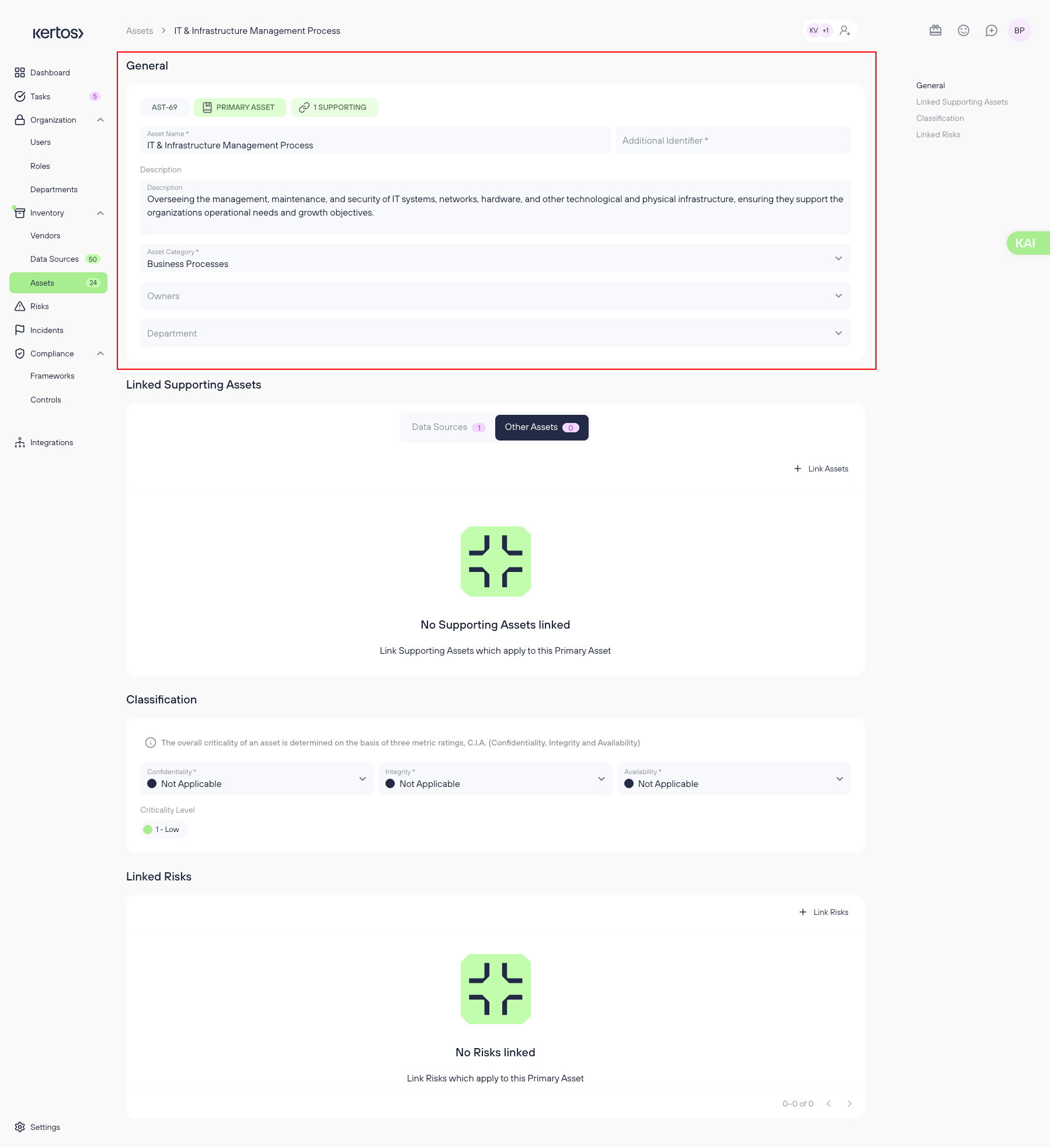
Required Information:
- Asset Name: The name of the asset.
- Asset ID: A unique identifier for tracking the asset.
- Classification: The importance of the asset based on the CIA triad (Confidentiality, Integrity, Availability).
Optional Information:
- Owner: The responsible person for the asset.
- Department: The business unit that utilizes or owns the asset.
- Description: Any additional information relevant to the asset.
- Linked Supporting Assets: Displays all associated supporting assets (e.g., databases, software, cloud services) that process or store this Primary Asset.
- Linked Risks: Shows all identified risks related to the Primary Asset, ensuring visibility into potential vulnerabilities and their impact on business processes.
3. Assessing the Classification of an Asset
.png)
You can evaluate the Classification of a Primary Asset at the time of creation or by modifying an existing one.
- In the detail view of the asset, scroll down to “Criticality”.
- Provide ratings for each CIA component on a 1-4 scale, as explained in the interface.
- The Classification Level will be automatically calculated.
- Click Save to finalize the changes.
4. Linking Supporting Assets
Supporting Assets are systems or services that process or store Primary Assets (e.g., software, databases, cloud services). Linking these assets to Primary Assets helps you understand where and how critical information is processed.
Steps:
- Open the primary asset you want to add supporting assets to.
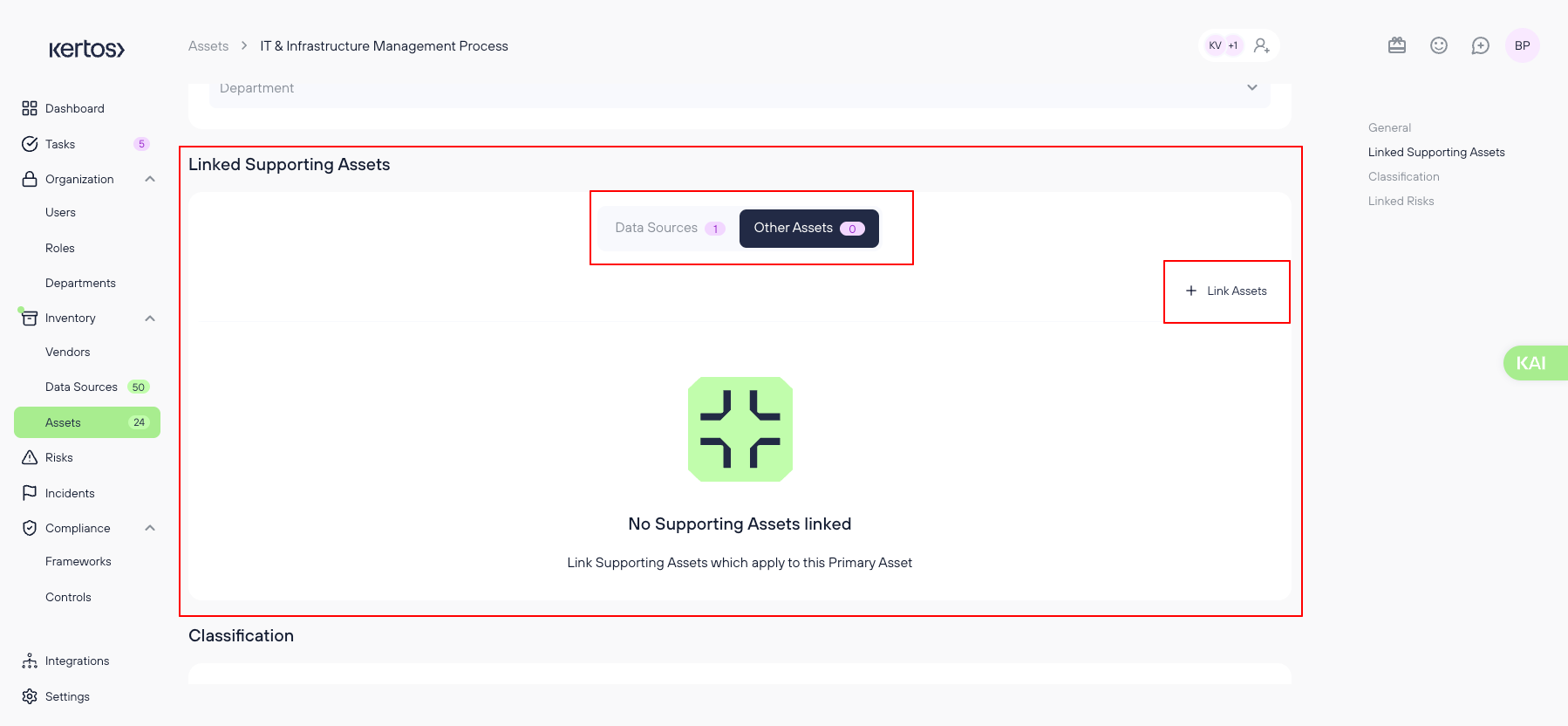
- Locate the "Linked Supporting Assets" section
- Select the "other assets"
- Click ‘+ Link Assets’.
- Select an asset from the suggested list or search for an asset in the system.
- Click Save to confirm the connection.
- Review Linked Assets
Once linked, the Supporting Asset appears in the table, displaying:
- Criticality Level (Low, Medium, High)
- Last Login (if applicable)
- Owner
- Category (e.g., Software, Cloud Service, Finance Tool)
5. Linking Risks to Primary Assets
To ensure a comprehensive risk assessment, it’s essential to link supporting risks to Primary Assets. This process allows users to understand the potential impact of risks on business-critical processes and ensure that appropriate security controls are in place.
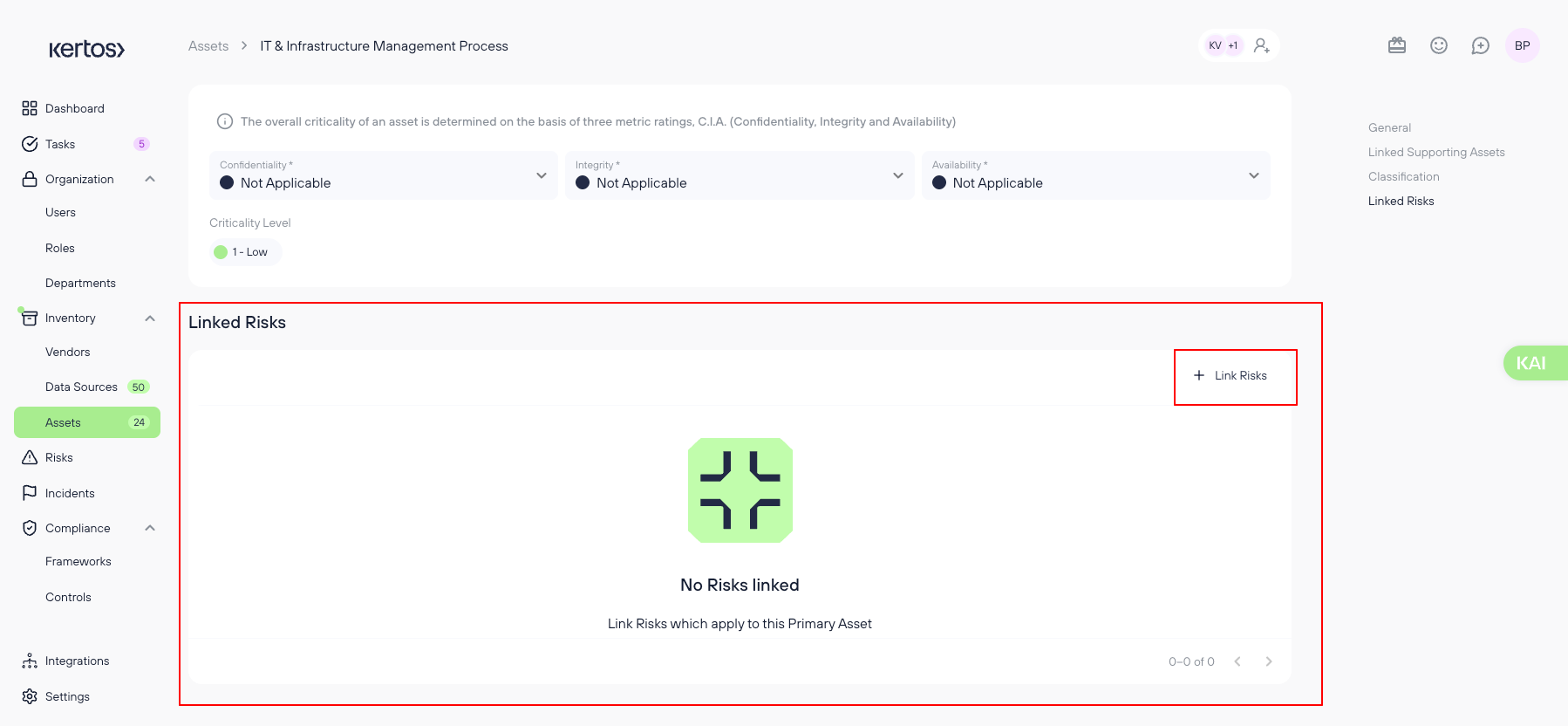
Steps:
- Open an existing Primary Asset (e.g., "Lead Scoring and Qualification").
- Locate the ‘Linked Risks’ Section
- Click ‘+ Link Risks’.
- Select a risk from the suggested list or search for an existing risk in the system.
- Click Save to confirm the connection.
- Review Linked Risks:
Once linked, the Risk will appear in the table, displaying the Risk Level (Low, Medium, High)
Best Practices for Managing Primary Assets
- Ensure completeness: Always provide Owners and Departments for clear accountability.
- Link risks and controls: Assess asset criticality to inform Risk Management decisions.
- Maintain consistency: Use structured naming conventions for better traceability.
6. Grouping assets together
Managing supporting assets efficiently is crucial for compliance and operational efficiency.
.png)
The Supporting Asset Groups feature enables you to create groups for better asset management within the Supporting Assets Table. At the top of the table, you can see category tags such as Business Devices, C-Level Devices, and Tech-Devices for easy organization.
Note: You need to select a subcategory before the feature appears. You cannot use this feature when you select the filter "All".
.png)
Steps:
- Clicking on a Supporting Asset Group will automatically select all listed assets within that group.
- You can then perform several bulk actions, including deleting, archiving, adding assets to another group, editing classifications, ungrouping, or renaming the group.
- You can now group hardware assets within the Supporting Asset Table under different subcategories (e.g., Computers, Smartphones). This feature enables two key bulk operations:
7. Bulk Classification Assignment
.png)
You can assign a classification to an entire asset group at once, ensuring consistency and reducing manual effort.
Clicking on Edit Classification will open a window where you can evaluate and update the classification level for the selected assets.
8. Bulk Linking to Primary Assets
.png)
- To link a group of supporting assets to a primary asset, follow the same steps from linking supporting assets as described above.
- Select an entire asset group instead of a singular asset
Frequently Asked Questions (FAQs)
Q1: What are Assets?
A: Assets are resources that hold value for your organization. These include physical assets like computers, servers, and software, as well as intangible assets like data, intellectual property, and processes.
Q2: What do I need to do in the ‘Assets’ section?
A: Keep the asset section up-to-date, ensure all necessary information is documented, and reflect changes as they occur. This forms the basis for compliant risk management.
Q3: What do I need to do with discovered assets?
A: Assess whether the discovered asset is relevant to your organization. If it is, move it to Active and fill out the required details. If not, move it to the Archive.
Q4: Which information fields for assets are mandatory?
A: The Asset Name, Asset ID, and Classification fields are mandatory. It's also mandatory to assign an Owner and Holder, if applicable.
Q5: Which assets do I need to add to the asset inventory?
A: Add all assets relevant to your organization that could pose a security or compliance risk.
Q6: What is the CIA assessment for?
A: The CIA assessment evaluates an asset's Confidentiality, Integrity, and Availability levels, helping you determine its criticality and assess the appropriate security controls.
Q7: How do I know that I have all assets?
A: Use Kertos' Discovery Integrations to automatically detect assets, but ensure that all important assets are documented manually as needed.
