Managing risks
Purpose
Manually managing information security risks across different departments and frameworks is complex, error-prone, and difficult to scale. Without a centralized and consistent risk assessment approach, it’s easy to overlook threats, duplicate effort, or fall short of audit requirements. This can be solved using the “Risks” section of the Kertos platform.
Capabilities
- Predefined Risk Templates: allow for quick risk creation and reduce manual entry
- Risk Matrix: provides a visual overview that helps prioritize risks based on likelihood and impact.
- Suggested Controls: offer automated recommendations based on risk context, making it easier to apply the right mitigations.
- Ownership Assignment: enables clear accountability by assigning one or more responsible individuals to each risk.
- Residual Risk Tracking: allows for reassessment after controls are applied, helping to evaluate treatment effectiveness.
How It Works
Risk Overview
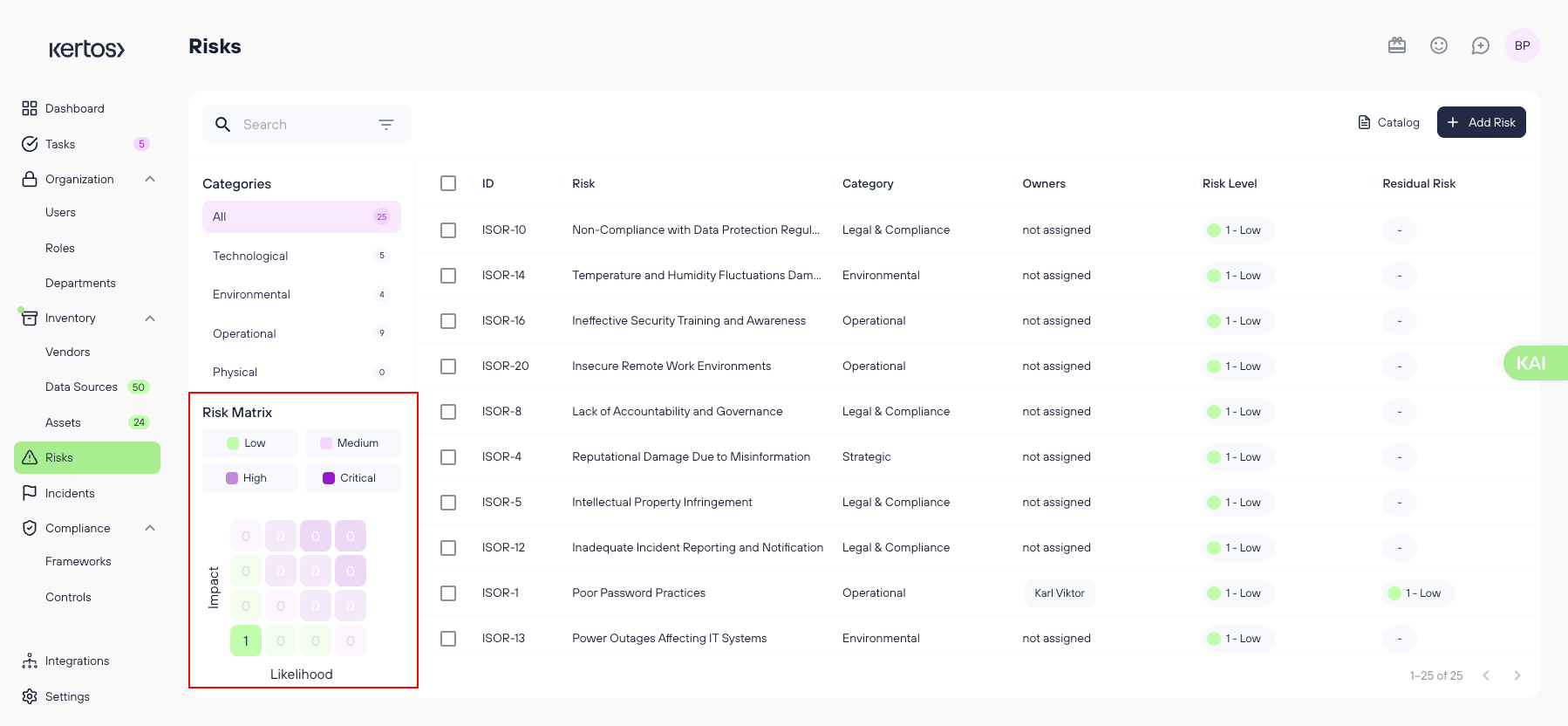
On the Risk Overview page, you'll find the following sections:
- Categories: Risks are grouped by context to help you navigate and manage them more easily.
- Risk matrix: This visual tool maps risks based on two dimensions - Impact and Likelihood. Click on any square in the matrix or on a risk level name to filter the list to that severity level.
- Overview: Displays a list of all added risks, along with key information about each. Clicking on any of the risks will open the Detail View for that risk.
Detail View
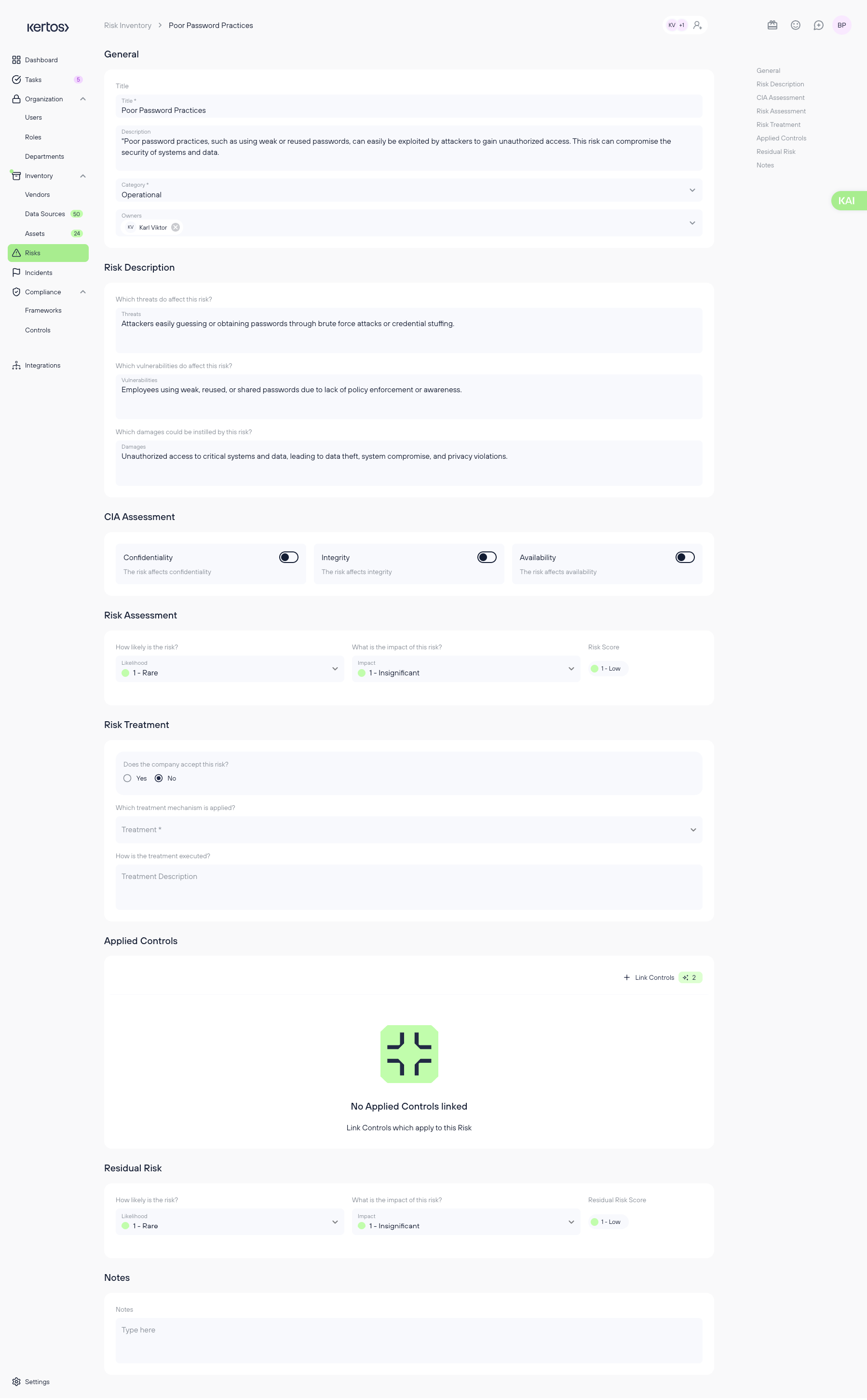
General
- Title: The name of the risk.
- Description: A detailed explanation of the risk.
- Risk category: The context or area of the organization where the risk occurs.
- Owners: The individuals responsible for managing the risk. These should be people who are operationally close to the risk’s context and capable of accurately assessing and addressing it.
Risk Description
- Threats: What potential dangers could affect your company?
- Vulnerabilities: What weaknesses could be exploited?
- Damages: What consequences might arise if the vulnerabilities are exploited?
CIA Assessment
Specify which components of the CIA triad are affected by the risk (multiple selections allowed):
- Confidentiality
- Integrity
- Availability
- Authenticity (available only for clients with a DORA subscription, as required by the DORA regulation)
Risk Assessment
- Likelihood: How likely is it that this risk will materialize? (Rated from 1 = Rare to 4 = Likely)
- Impact: How severe would the consequences be? (Rated from 1 = Insignificant to 4 = Catastrophic)
- Risk Score = Likelihood x Impact
Risk Treatment
- Acceptance: Has the company decided to accept the risk?
- If yes, no further treatment details are required.
- If no, proceed to define the treatment mechanism.
- Treatment Mechanism: Will the risk be avoided, mitigated, or transferred (e.g., through insurance)?
- Treatment Description: A detailed explanation of how the risk is being addressed in your organization.
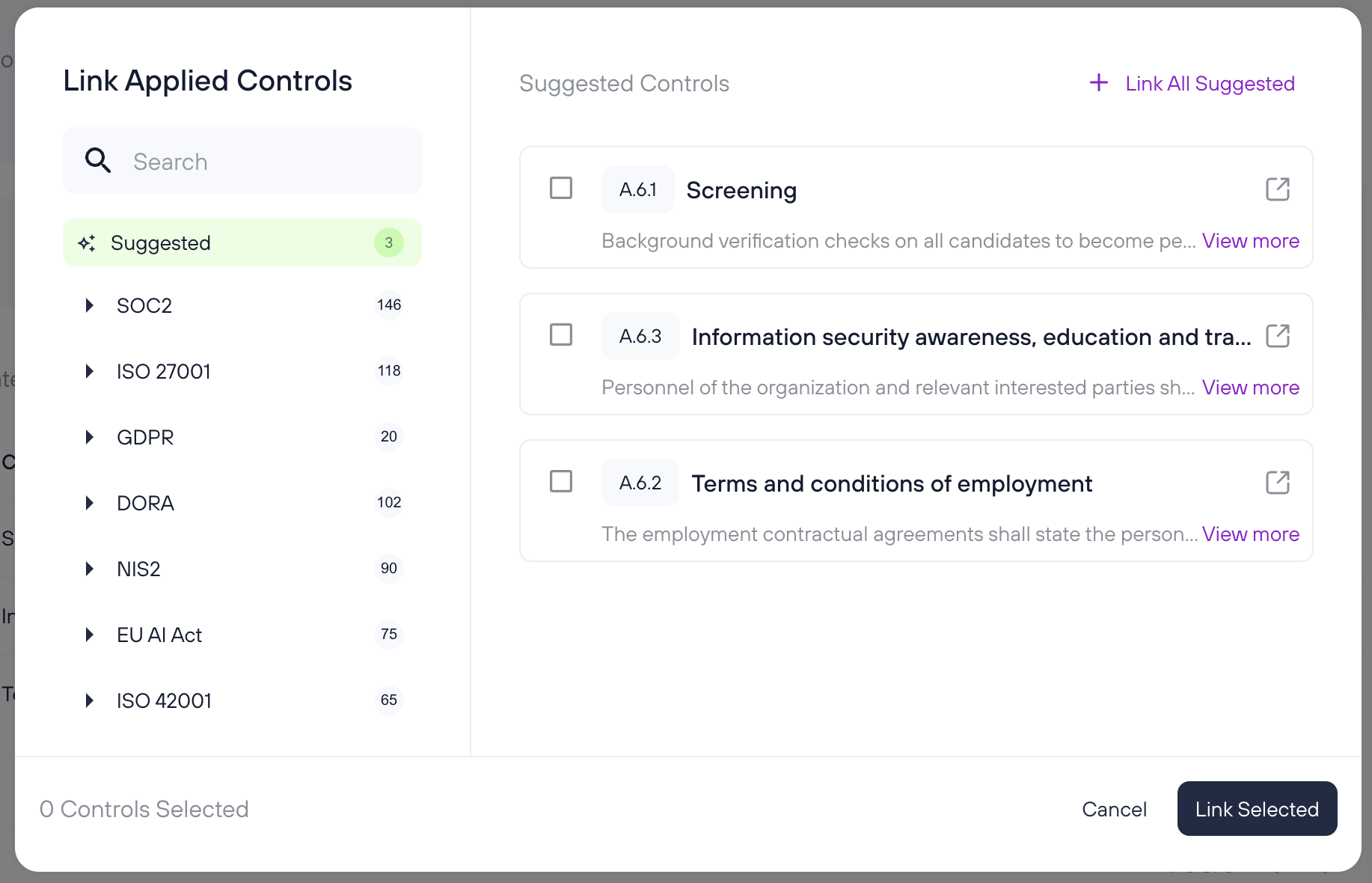
Applied Controls
This section allows you to link controls to the risk:
- Click “Link controls” to open a window where you can select controls from various frameworks.
- On the right-hand side, you’ll see “Suggested Controls” automatically recommended based on the characteristics of the risk.
- You can either click “Link All Suggested” to quickly add all recommended controls or manually select specific ones and press “Link selected”.
Residual Risk
- Re-assess the Likelihood and Impact of the risk after the treatment and controls have been applied. The scoring method remains the same as in the initial Risk Assessment.
Notes
- Use this field to add any additional information or context relevant to the risk.
Documenting Risks
In the Risks tab, you can add and manage risks either by selecting predefined risks from the Catalog or by creating them manually. Both methods allow you to document key risk information and ensure a structured and compliant risk assessment process.
Adding risks from the Catalog
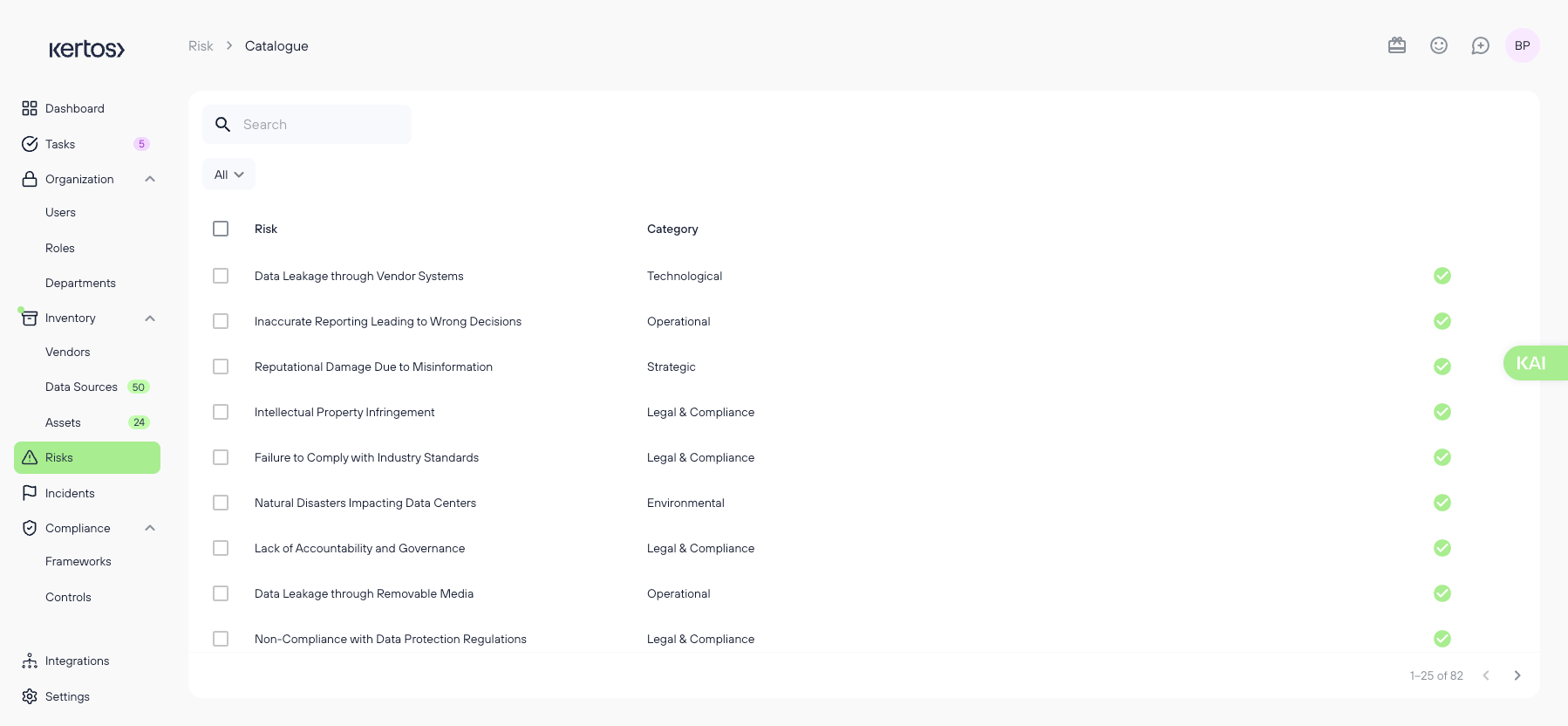
1. Select the category you want to add risks for.
2. Browse the list and preview any risk by clicking on it.
3. Select individual risks or use the checkbox at the top to select all.
4. Click “Add selected” to create these risks.
5. The added risks will appear in the overview.
Adding risks manually
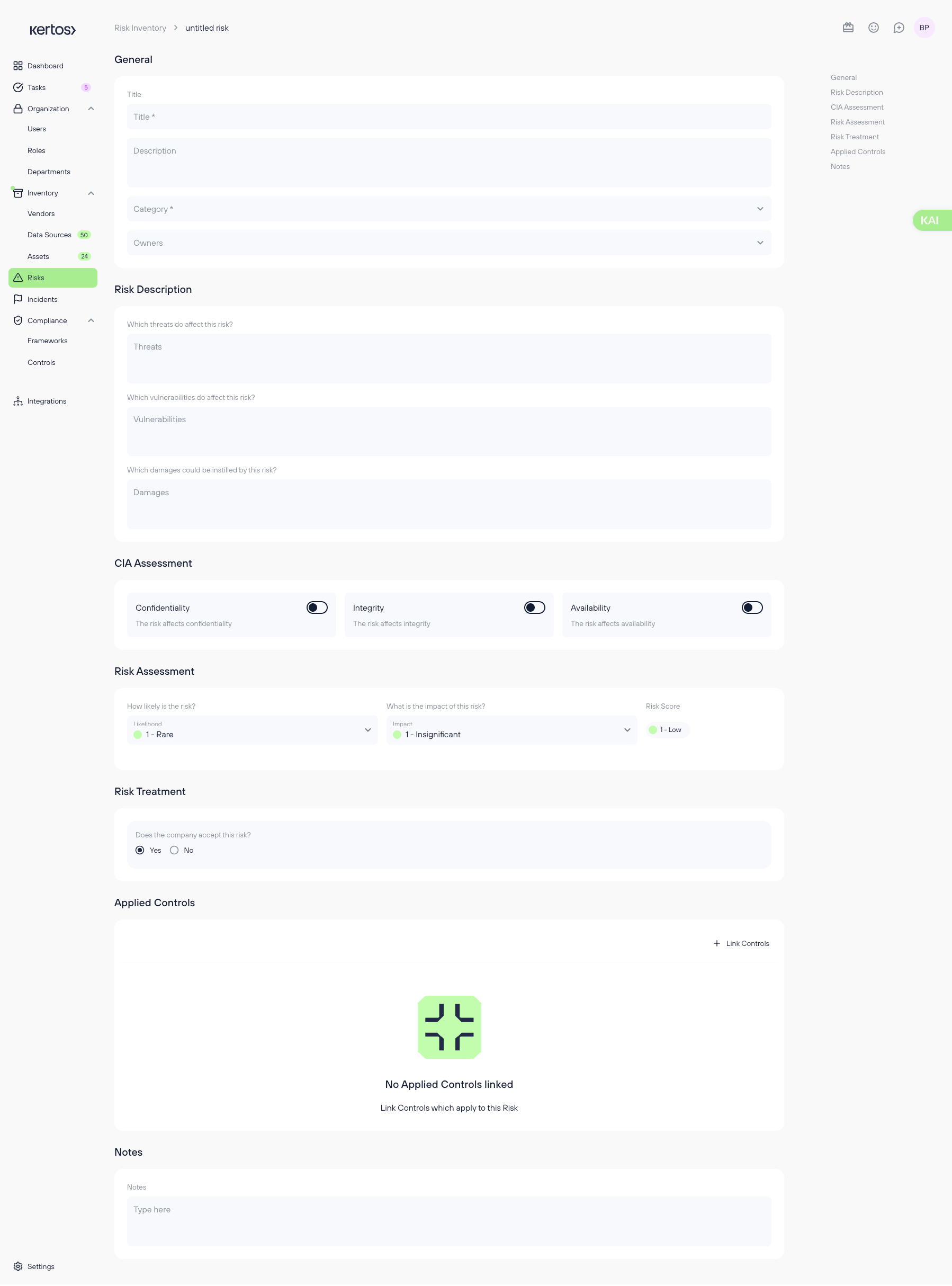
1. On the overview page, click “Add Risk” in the top right corner.
2. You’ll be taken to the Detail View of a new, empty risk.
3. Fill out all required fields (as described in the Detail View section) and click “Save” when finished.
FAQs
How do I know which risks apply to my organization?
Start with the Risk Catalog for a curated list of common risks across categories. You can preview and select relevant ones, or ask KAIA for guidance if you’re unsure. It's also best practice to derive risks from your assets, assuming your asset inventory is complete.
What’s included when I add a risk from the catalog?
Catalog risks come with a predefined title, description, threats, vulnerabilities, and potential damages. You’ll still need to assign owners, complete the risk and CIA assessments, define treatment, and link applicable controls.
Can I edit catalog risks after adding them?
Yes. Once added, catalog risks behave like manually created ones - you can customize all fields to reflect your company’s specific context.
Do I need to include all controls immediately when creating a risk?
Not necessarily. Once a risk is added, open its Detail View and scroll down to the Applied Controls section. Click “Link Controls” to view expert-recommended controls. You can either apply them all using “Link all suggested” or pick specific ones to “Link selected.”
Is it better to assess risks before or after implementing controls?
You should assess risks based on your current situation, including any controls already in place. This gives an accurate picture of your security posture and helps measure control effectiveness.